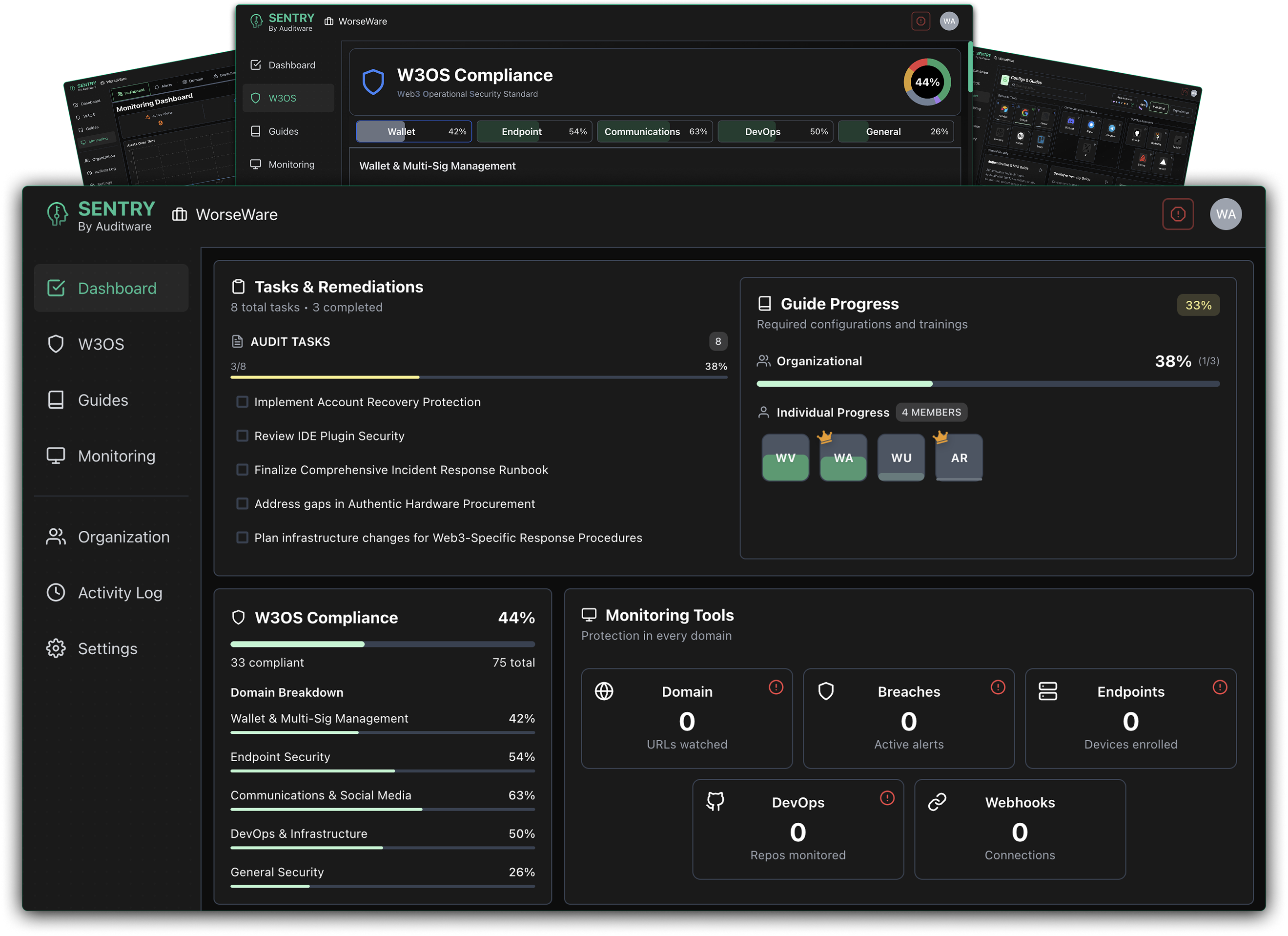
Monitor endpoints and devices for signs of compromise and unauthorized access.
Example signals: Unusual login locations, device policy violations, suspicious process execution.
Track identity and access management for account security and permissions.
Example signals: Privilege escalation, inactive account access, MFA bypass attempts.
Watch DevOps pipelines and GitHub repositories for suspicious changes.
Example signals: Unauthorized repo access, secret exposure, CI/CD configuration changes.
Monitor frontend applications and DNS records for tampering and attacks.
Example signals: DNS record modifications, certificate changes, frontend injection attempts.
Breach detection
Monitor compromised credentials and organizational email exposure across dark web sources.

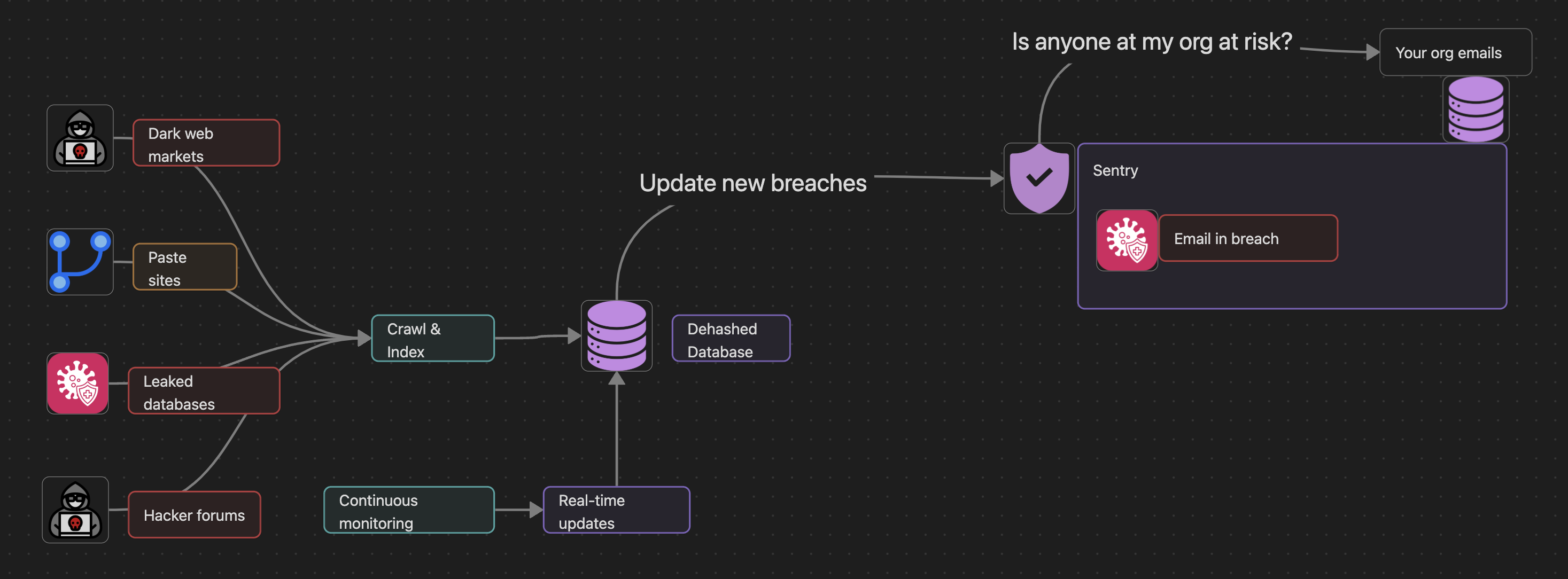
Real-time alerts when organizational emails appear in breach databases.
Continuous monitoring of dark web markets, paste sites, and leaked databases feeds into Sentry's threat detection engine.
GitHub monitoring
Detect malicious activity and developer mistakes across your organization's repositories.
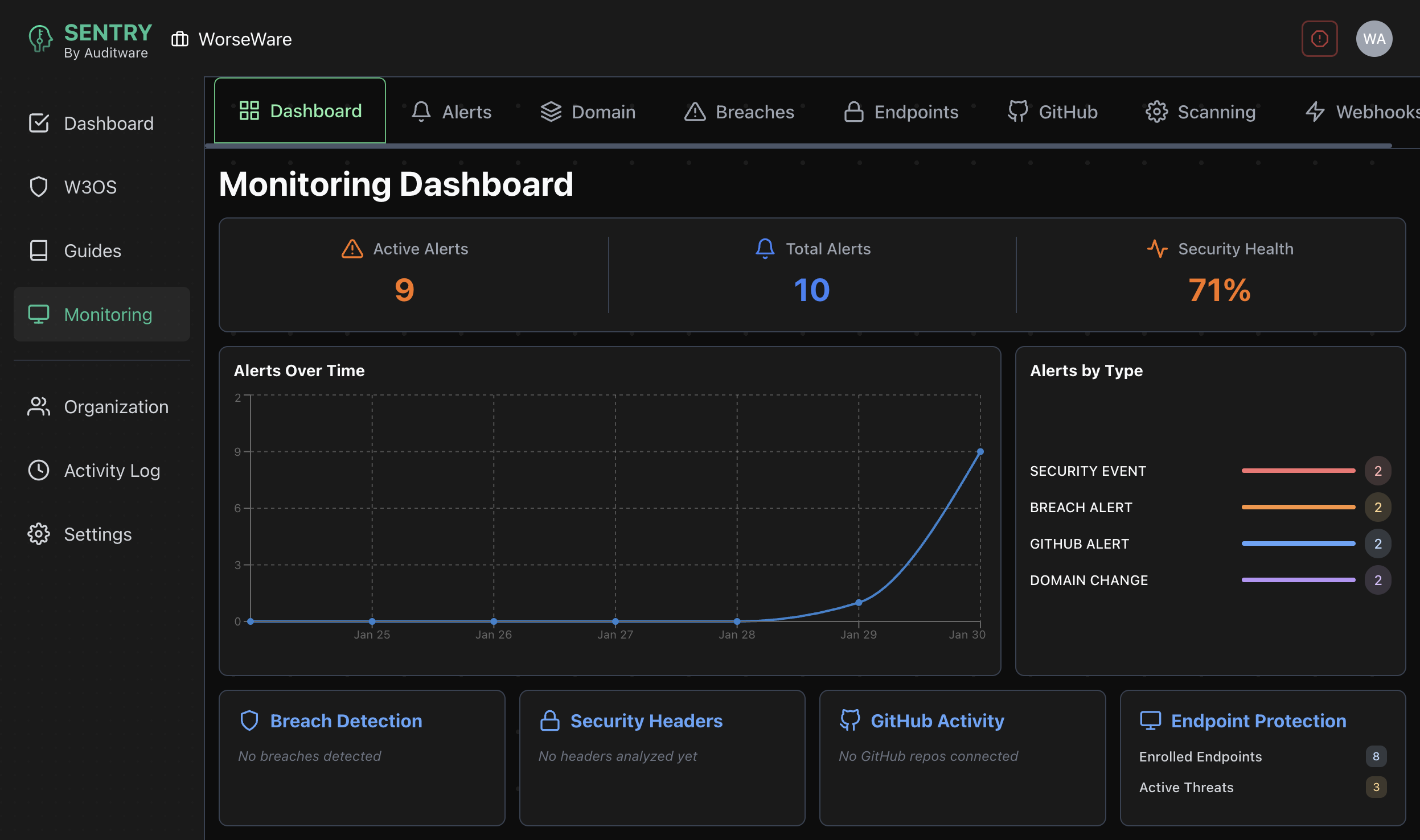
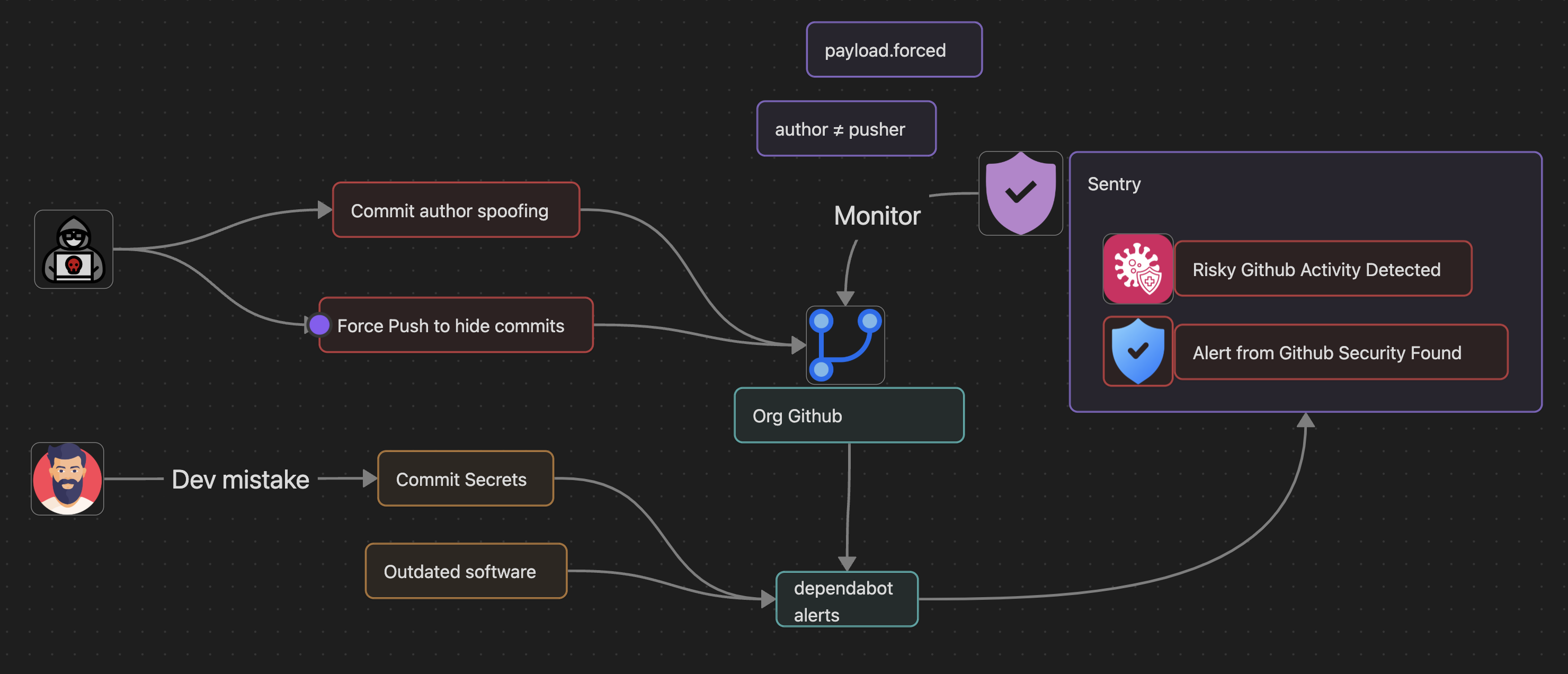
Alerts on risky GitHub activity including commit author spoofing and force pushes.
Monitors for commit author spoofing, force pushes, secret exposure, and outdated dependencies.
Frontend security
Monitor website content changes and security header configurations to detect tampering.
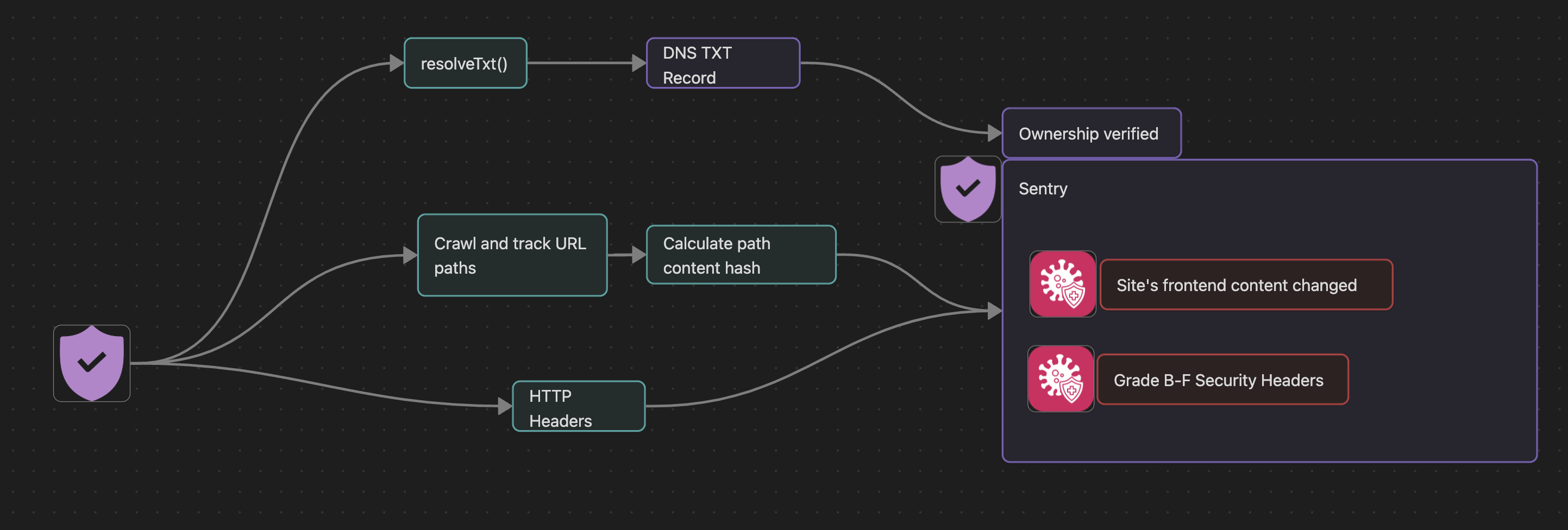
Alerts when frontend content changes or security headers degrade.
Tracks DNS TXT records for ownership verification, URL path content hashes, and HTTP security header grades.
Endpoint protection
Continuous monitoring of endpoints and devices for compromise indicators and policy violations.
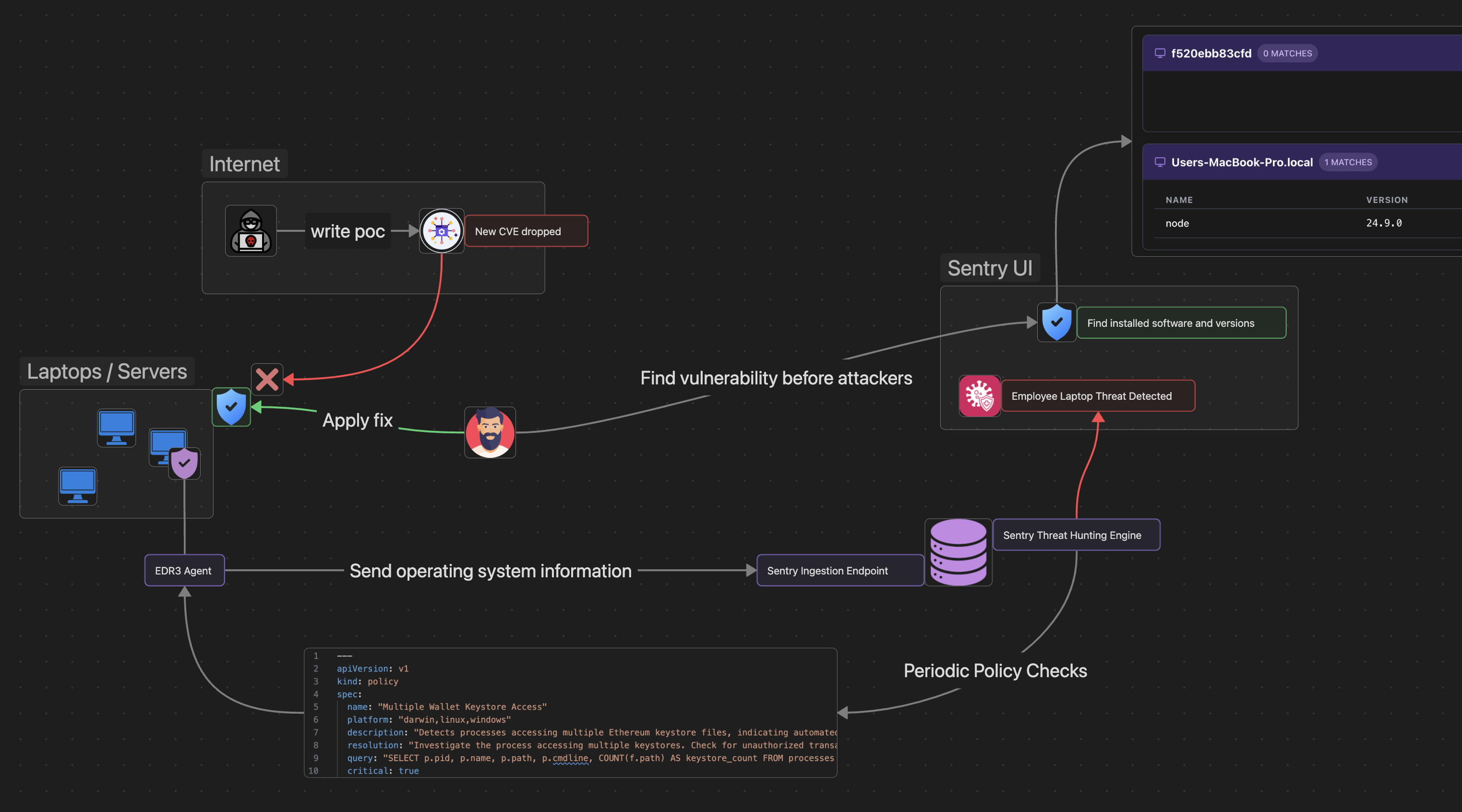
Real-time device monitoring with software inventory and threat detection.
EDR agents send OS information to Sentry, which performs policy checks and detects vulnerabilities before attackers exploit them.
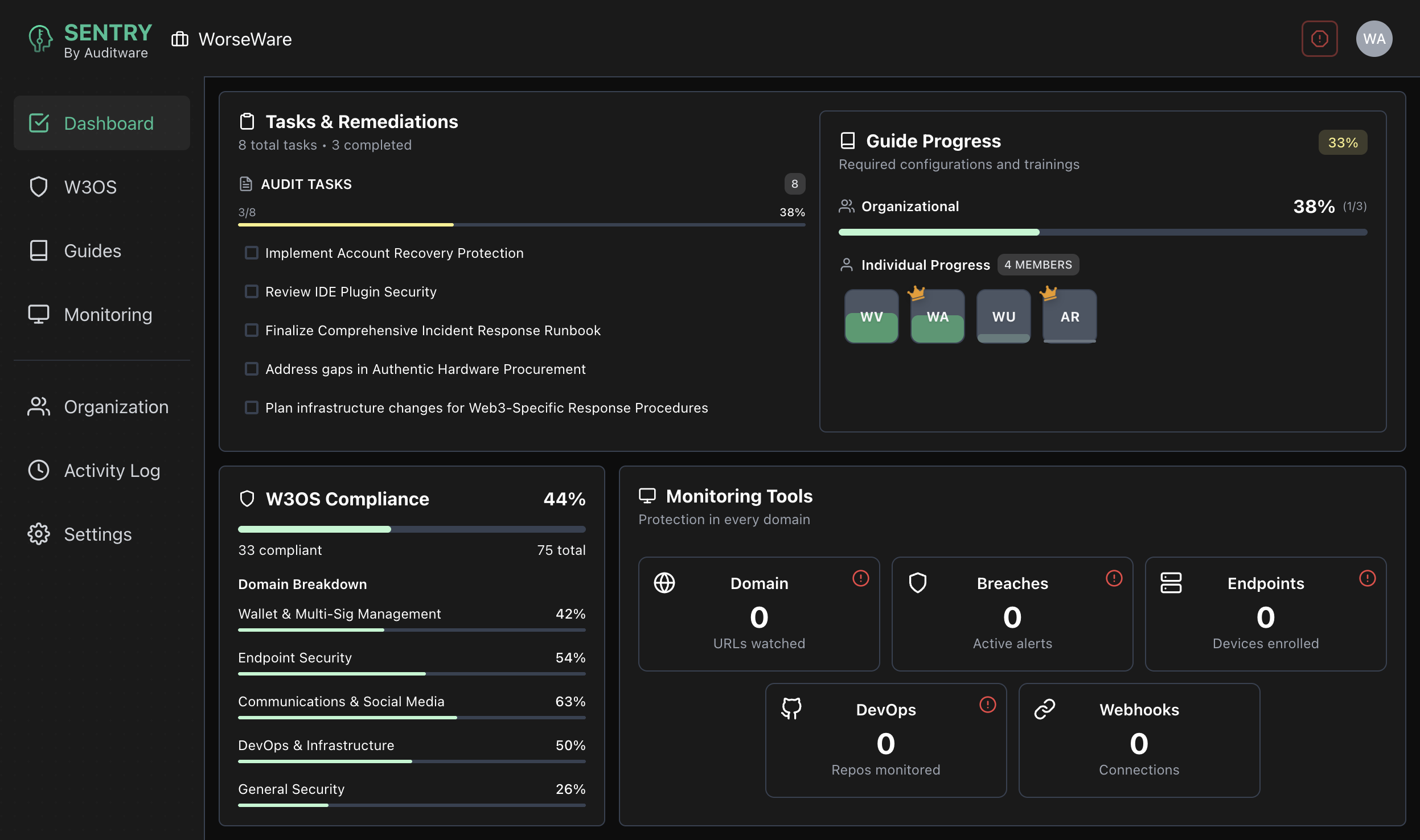
Access Sentry or talk to the team about continuous OpSec monitoring. Book an operational security audit to identify and mitigate risk.